Software Restriction Policies:
Software restriction policies can help organizations protect themselves because they provide another layer of defense against viruses, Trojan horses, and other types of malicious software. You can configure the Software Restriction Policies settings in the following location within the Group Policy Management Console:
Computer Configuration\Windows Settings\Security Settings\Software Restriction Policies
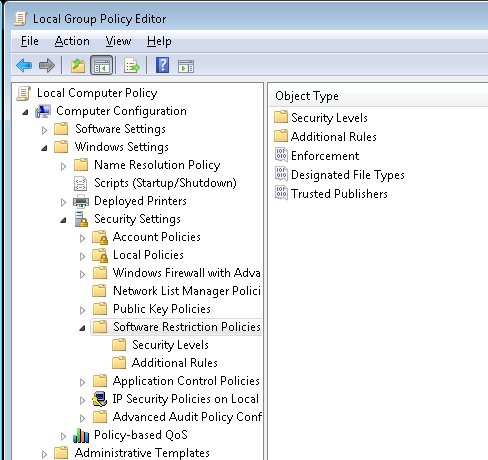
Software restriction policies do not prevent restricted processes that run under the System account. For example, if a malicious program has set up a malicious service that starts under the Local System account, it starts successfully even if there is a software restriction policy configured to restrict it. A flawed software restriction policy implementation can disable necessary applications or allow malicious software to run.
A policy consists of a default rule that specifies whether programs are allowed to run and exceptions to that rule. The default rule can be set to Unrestricted (the program is allowed to run) or Disallowed (the program is not allowed to run). Setting the default rule to Unrestricted allows an administrator to define exceptions (programs that are not allowed to run). A more secure approach is to set the default rule to Disallowed, and specify only the programs that are known and trusted to run.
There are two ways to use software restriction policies:
A software restriction policy supports the following four ways to identify software:
Administering AppLocker
Understanding AppLocker Rules and Enforcement Setting Inheritance in Group Policy
Software restriction policies can help organizations protect themselves because they provide another layer of defense against viruses, Trojan horses, and other types of malicious software. You can configure the Software Restriction Policies settings in the following location within the Group Policy Management Console:
Computer Configuration\Windows Settings\Security Settings\Software Restriction Policies

Software restriction policies do not prevent restricted processes that run under the System account. For example, if a malicious program has set up a malicious service that starts under the Local System account, it starts successfully even if there is a software restriction policy configured to restrict it. A flawed software restriction policy implementation can disable necessary applications or allow malicious software to run.
A policy consists of a default rule that specifies whether programs are allowed to run and exceptions to that rule. The default rule can be set to Unrestricted (the program is allowed to run) or Disallowed (the program is not allowed to run). Setting the default rule to Unrestricted allows an administrator to define exceptions (programs that are not allowed to run). A more secure approach is to set the default rule to Disallowed, and specify only the programs that are known and trusted to run.
There are two ways to use software restriction policies:
- If an administrator knows all of the programs that should run, then a software restriction policy can be applied to allow only this list of trusted applications.
- If all the applications that users might run are not known, then administrators can disallow undesired applications or file types as needed.
A software restriction policy supports the following four ways to identify software:
- Hash: A cryptographic fingerprint of the file.
- Certificate: A software publisher certificate that is used to digitally sign a file.
- Path: The local or universal naming convention (UNC) path of where the file is stored.
- Zone: The Internet zone as specified through Internet Explorer.
Applocker:
You can configure application restrictions in Windows 7 by using a tool called Applocker. With it you can configure Application Control Policies, which allow you to block the execution of a program by file name or hash calculation. Applocker helps you to allow the applications you want, and block the rest. But AppLocker is present only in the Enterprise and Ultimate editions of Windows 7. Applocker provides the following functionalities:
You can configure application restrictions in Windows 7 by using a tool called Applocker. With it you can configure Application Control Policies, which allow you to block the execution of a program by file name or hash calculation. Applocker helps you to allow the applications you want, and block the rest. But AppLocker is present only in the Enterprise and Ultimate editions of Windows 7. Applocker provides the following functionalities:
- Prevent unlicensed software from running in the desktop environment if the software is not on the allowed list
- Prevent vulnerable, unauthorized applications from running in the desktop environment, including malware
- Stop users from running applications that needlessly consume network bandwidth or otherwise affect the enterprise computing environment
- Prevent users from running applications that destabilize their desktop environment and increase help desk support costs
- Provide more options for effective desktop configuration management
- Allow users to run approved applications and software updates based upon policies while preserving the requirement that only users with administrative credentials can install or run applications and software updates
- Help to ensure that the desktop environment is in compliance with corporate policies and industry regulations
- AppLocker introduces publisher rules that are based upon application digital signatures. Publisher rules make it possible to build rules that survive application updates by being able to specify attributes such as the version of an application.
- Click Start and type gpedit.msc into the search box.
- In Local Computer Policy go to Computer Configuration \ Windows Settings \ Security Settings \ Application Control Policies \ AppLocker. Here you can see overall controls for the applications.
- In the Configure Rule Enforcement window, click the Configure rule enforcement link.
- In Applocker properties Window, click the checkbox for Executable Rules, Windows Installer Rules, or Script Rulesdepending on which type of application you are trying to control (in this example, we selected Executable Rules). Click OK.
- In the Overview window, click the Executable Rules.
- Right-click and select Create New Rule. This opens up the Create Executable Rules wizard and you can select not to show the introduction screen at start up for the next time you access it by clicking the checkbox skip this page by default.
Select Permissions under Action, select Deny. Add the user name for whom you want to block the application.
In Conditions you can select from Publisher, Path or File hash, whichever you want to block. For example, if you want to block games, for example, select Path. Click Next.
- Click Browse Folders and select the Microsoft Games folder. If you wanted to block a specific game(s) only, you would click on Browse Files and select the games in you wanted blocked.
- On the next screen you can add Exceptions like allowing certain applications.
- Add a description to the rule, and click Create and then click Yes.
- After creating the rule, start Application Identification and set it to automatically, otherwise the rules won’t work. By default this service is not started so you need to enable it.
Administering AppLocker
Understanding AppLocker Rules and Enforcement Setting Inheritance in Group Policy







No comments:
Post a Comment